About
Who we are
A global Cyber Security and AI Innovation Hub working with clients and partners to address current business challenges by exploring the potential of emerging technologies.
- Over 25 Years of Experince in working with emerging technologies like AI, Machine Learning, Internet of Things, Blockchain and others
- Support with regulatory compliance around Cyber Security and Data Protection including ISO 27001, PCI DSS, GDPR, LGPD and others
- Cerified Information Security Auditors, ISO 27001 and CREST Accredited
- Approved UK Crown Commercial Services Suppliers
Over 15 years experience in implementing standards and regulatory requirements around information security and data privacy including GDPR. A clear understanding of Information Security and Data Privacy provides a strong underpinning when looking at potential use cases and defining some of the compliance and ethical considerations that might arise
INFINITECH is a joint effort of global leaders in Digital Technologies and Financial Services
Working towards lowering the barriers for BigData / IoT/ AI driven innovation, boosting regulatory compliance and stimulating additional investments
- Novel BigData/IoT technologies for seamless management and querying of all types of data interoperable data analytics, blockchain-based data sharing, real-time analytics, as well as libraries of advanced AI algorithms.
- Regulatory tools incorporating various data governance capabilities and facilitating compliance to regulations (e.g., PSD2, 4AMLD, MIFiD II).
- Nine novel and configurable testbeds & sandboxes, each one offering Open APIs and other resources for validating autonomous and personalized solutions, including a unique collection of data assets for finance/insurance.
Despite rising investments in Big Data, AI and IoT in finance and insurance, a set of challenges still must be overcame to improve the overall efficiency of business processes and optimize decision making in the finance and insurance sectors. Infinitech provides support to overcome Regulatory barriers, the lack of datasets, testbeds and validated business models that otherwise prevent financial instiutions from realizing the full potential of these new technologies.

Secure, Privacy Preserving Data Soveriegnty
Persistent Personal Data Vaults empowering Secure and Privacy Preserving Data Storage, Soverignty, Sharing, Analysis and Monetisation
The lack of trusted, secure, ethical-driven personal data platforms and privacy-aware analytics, hinders the growth of the data economy and creates concerns.
- Holistic Personal Data Management
- Novel Data Security and Privacy Risk Assessment
- Twin-fold Data Brokerage Engine
- Edge and Centralised Analytics
- Privacy Preserving and Data Secure Retention Mechanisms
- Smart Data Interlinking
Cryptography, data anonymisation, remote attestation and trusted data exchange with TPM technologies between the Personal DataVaults and the DataVaults cloud-based engine. Privacy risk assessment for individuals revealing the true risk exposure factor of individuals based on the shared data

Integrated Framework for Predictive and Collaborative Security of Financial Infrastructures
An integrated, intelligent, collaborative and predictive approach to the security of critical infrastructures in the financial sector. A novel reference architecture for integrated physical and cyber security of critical infrastructures, which enables handling of dynamic, advanced and asymmetric attacks, while at the same time boosting financial organizations’ compliance to security standards and regulations.
- Integrated Cyber and Physical Security
- Predictive Security for Critical Infrastructures
- Security Data Sharing and Information Exchange based on Distributed Ledger Technologies and Smart Contracts
FINSEC's collaborative approach is based on stakeholders' collaboration across the financial services supply chain in the identification, assessment and mitigation of risks, including their cascading effects.

Stakeholders will formulate a distributed network of existing and new data spaces with built-in governance brought by PISTIS to eliminate silos while accruing the actual data value and multiplying it through derivative assets in a fair and transparent manner.
- Federated Data Management, Interoperability & Governance
- Federated, Secure Data Sharing that concerns the effective management and on-chain storage of (multi-party) data contracts
- Data Valuation and Monetisation to systematically articulate and recommend an appropriate target value, indicatively taking into consideration the “cost” approach, the “income” approach, and the “market” approach

Patented Searchable Encryption to search and gather insight from data whilst maintaining complete privacy and security
Allows Cloud Service Providers, Enterprises and their clients to store encrypted data on the Cloud while being able to search over it. This pioneering solution gives users full control over the data stored on the Cloud. Our state-of-the-art Searchable Encryption solution reduces the network latency and the storage overhead, whereas, it is scalable across cross-cloud platforms. Hence, CityDefend has a profound impact across different verticals including Financial, Healthcare, Telecommunication, Legal Services, government and the Law Enforcement sectors. Our offering includes an API and a Cloud Integrated Desktop Application.
A new concept using probabilistic (non-deterministic) search queries which prevents any search pattern leakage. Malicious attackers are unable to infer any information about the query or the dataset, hence the system is immune to statistical attacks.
- Security and privacy are increased as the technology is based on a state-of-the-art encryption technique
- Manage and mitigate risks. CityDefend’s privacy preserving search capability enables targeted searching across distributed storage media, while integrating with access control policies
- Improve data governance. CityDefend facilitates data governance strategies by increasing data integrity and availability through secure sharing, and reducing the frequency and impact of breaches

Detect and Respond to API security threats across all your API traffic in real time
Monitors all your API traffic: between the client and server (North-South traffic), and between API endpoints (East-West traffic). It screens each call to determine anomalous patterns and threat indicators, and detect API credential theft, compromised accounts and authentication bypass attacks.
Inspects every API call for misuse. It uses AI techniques such as machine learning and deep learning to perform behavioural analytics, and provide adaptive risk assessments in real time. If the risk is too high, the request is denied — and your systems stay secure.
- Monitor and detect threats across all API traffic
- Stop risky requests in real time
- Receive instant updates on threats, prioritise privacy and grow your business through an improved security posture

Cyber Risk Quantification: Empowers Underwriters, Insurers, CISOs, CFOs and other senior executives to quantify and manage cyber risk at a strategic level
Benchmark your security maturity against similar organizations. Identify gaps, prioritize improvements, and justify investments with data-backed insights. With comparisons based on over 4,500 risk assessments, you get a clear, objective view of where you stand and how to strengthen your defenses.
Answer simple questions to determine your organization's inherent exposure to cyber risk based on factors such as industry, geography, size, and IT/OT dependencies. This will serve as a baseline for understanding your risk profile.
- Get data-driven recommendations on whether you're over- or underinvesting in critical areas and prioritize actions to effectively improve your risk balance.
- Demonstrate clear progress toward risk management goals with easy-to-understand visualizations. Squalify provides the tools you need to effectively communicate your cybersecurity strategy at the board level.
- Helps organizations measure and manage cyber risk in financial terms
- Stop guessing. Make smarter decisions faster with clear, actionable recommendations tailored to your unique risk profile.
Complete visibility into your sensitive data with efficient data discovery, classification, and risk analysis.
Simple to deploy and use, it provides you with a single pane of glass that allows you to get a clear understanding of what sensitive data you have, where it’s located, and its risks of exposure. With rich visualizations and detailed reports, you can more easily uncover and close your gaps, make better decisions about third-party data sharing and cloud migration, and proactively respond to data privacy and security regulations like GDPR, LGPD,CCPA, PCI DSS and HIPAA
Efficiently identifies structured as well as unstructured sensitive data on-premises and in the cloud. Supporting both agentless and agent-based deployment models, the solution provides built-in templates that enable rapid identification of regulated data, highlight security risks, and help you uncover compliance gaps. A streamlined workflow exposes security blind spots and reduces remediation time
- Effective solution for enterprise-wide data privacy
- Complete visibility and control
- Accelerated path to compliance
- Single pane of glass from discovery to remediation
Digitally-enabled construction planning and management solution that delivers step-change productivity improvements for on-site construction.
An analysis engine that uses AI-based algorithms (applied to filtered/triaged data feeds from on-site monitoring devices) to generate targeted information on critical construction tasks in near real-time. The resulting information streams are integrated into lookahead planning, enabling site mangers to rapidly react to evolving issues, avoiding time/cost-critical delays by rescheduling activities or reallocating resources. The project will develop a pre-commercial 'minimum-viable-product' solution for rapid deployment and which can be enhanced over time.
- Applies AI-based algorithms to on-site monitoring data feeds to generate task-specific information on task status in near real-time
- It enables site mangers to rapidly react to evolving issues, avoiding time/cost-critical delays by rescheduling activities or reallocating resources
- Game-changing solution that creates targeted information on construction task progress, enabling project managers to address evolving issues, rapidly reacting to reschedule activities or reallocate resources

TRAMS-AI Empowering Trusted, Responsible AI Innovation
A framework (rules, guidance) to manage trusted and responsible data, artificial intelligence, and machine learning-based solutions. TRAMS-AI provides tools for data governance that enable secure and compliant data management, ensuring data quality, integrity, and traceability throughout its lifecycle. It also offers bias detection and fairness assessment capabilities, leveraging algorithms to identify and mitigate biases in datasets and models, thereby promoting equitable outcomes. Additionally, TRAMS-AI incorporates explainability tools that make AI and ML models more interpretable, allowing users to understand how decisions are made and fostering transparency
To further enhance trust and accountability, TRAMS-AI includes robust monitoring and auditing mechanisms that continuously evaluate the performance and impact of AI systems in real-world applications
- These technologies ensure that models remain accurate, reliable, and aligned with ethical guidelines over time
- TRAMS-AI supports compliance automation, helping organizations adhere to evolving regulatory frameworks such as GDPR, AI Act, and other industry-specific standards.
- TRAMS-AI empowers organizations to implement a comprehensive framework for managing AI and ML solutions responsibly.
NexusFL Empowering Privacy Preserving Machine Learning
In a variety of domains across society, data owners have valid concerns about the risks associated with sharing their data, such as legal risks, privacy invasion (misuing the data), or intellectual property (copying and redistributing it). NexusFL enables data scientists to answer questions without even seeing or acquiring a copy of the data, within the data owners's definition of acceptable use. We call this process Remote Data Science.
This means that the current risks of sharing information with someone will no longer prevent the vast benefits such as innovation, insights and scientific discovery. With NexusFL data owners are able to enable 1000x more accesible data in each scientific field and lead, together with data scientists, breakthrough innovation.
- Decentralized Model Training: Federated Learning enables training machine learning models across multiple devices or servers without transferring raw data to a central location, preserving data privacy and security.
- Collaborative Learning: Models are trained locally on distributed datasets, and only model updates (e.g., gradients) are shared and aggregated to improve the global model, fostering collaboration without data sharing.
- Efficiency and Scalability: Reduces the need for large-scale data centralization, making it ideal for applications like healthcare, IoT, and edge computing, where data is sensitive or geographically dispersed.

A library to audit data privacy in a wide range of statistical and machine learning algorithms
Machine learning is playing a central role in automated decision-making in a wide range of organizations and service providers. The data, which are used to train the models, typically contain sensitive information about individuals. Although the data in most cases cannot be released, due to privacy concerns, the models are usually made public or deployed as a service for inference on new test data.
For a safe and secure use of machine learning models, it is important to have a quantitative assessment of the privacy risks of these models, and to make sure that they do not reveal sensitive information about their training data. This is of great importance as there has been a surge in the use of machine learning in sensitive domains such as medical and finance applications.
- Supports different types of models, datasets and privacy games, which all need to be specified in a .yaml configuration file
- Tools to quantify and evaluate the privacy risks associated with machine learning models, such as susceptibility to membership inference attacks, helping organizations identify vulnerabilities.
- Offers actionable insights and mitigation strategies to enhance data privacy, ensuring models comply with regulatory standards like GDPR and CCPA while safeguarding sensitive information.

Resources
Our Report on Privacy Enhancing Technologies
Services
How we can further support you
Information Security
COBIT and ISO 27001 - Best practice for implementing an information security management system, and is recommended globally. Supported by the Assentian State-of-the Art Compliance Toolkit.
Governance and Quality Management
Based on ISO 9001 with seven quality management principles, we will help you to continually monitor and manage quality across all of your operations, as well as benchmarking your organisation’s performance and service.
Data Security and Privacy
Support and management of compliance with Data Protection Regulations like GDPR, LGPD and US Privacy Shield. Access to the latest innovative tools and technologies to support real-time protection against sensitive data breeches
Identify and Authenticate Systems
Enforce authentication services like one-time passwords (OTPs) to web admin, User Portal, and more. Enforce specific end user policies, such as for DLP, device control, and more. Enforce encryption and password policy
Restrict Access to Personal Data
Granular, policy-based control over users, apps, web, and content to limit access to personal data based on business need-to-know. Role-based management separates authorization levels and detailed logging of all access attempts
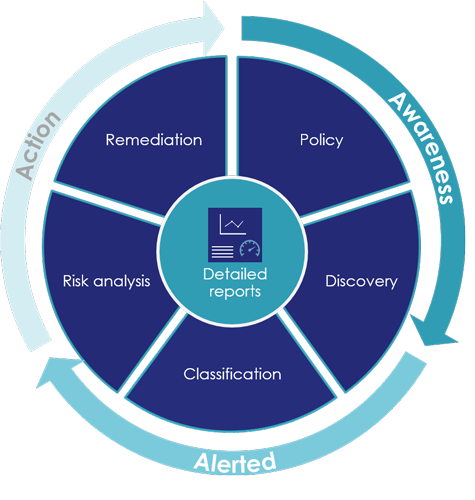
Business Continuity and Disaster Recovery (BCDR)
Services to develop, deploy, test and manage a holistic BCDR approach from creating a strategy for achieving resiliency, through to impact analysis, risk analysis, tests, exercises and ongoing management.
Call To Action
Find out about the level of Cyber Maturity and Data Security in your organisation by taking a free assessment. For Singaporean Users please contact us directly for access to the local version
End-to-End Secure Privacy Preserving AI: Conformity Analyis, AI Risk Management, Threat Modelling, Data Profiling, Model Evaluation, Privacy Preserving AI and more.
Spinouts
Innovative Technologies
A decision-making platform for a real-time, integrated and omniscient supply chain. Plan, Track, Automate, Analyse and Optimise Complex Global Supply Chains. Enforce Fiscal Compliance and Trade Agreements. Support end-to-end Traceability providing irrefutable provenance and origin of goods compliance
Innovative transformational technology to support sustainable growth in global trade in the Food and Agriculture Sectors - grow your market share, access new markets, enhance sustainability and resilience of your business and sector, improve food security and standards and work towards the UN Sustainability Development Goals
Innovation
Access to and Development of Innovative Products and Services
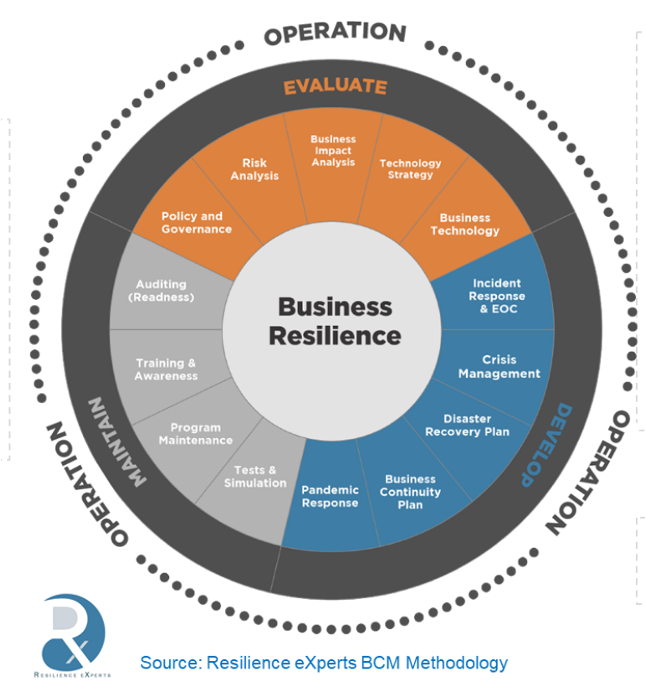
Becoming Resilient
Cyber and Business Resilience as a Service
-
Business Impact Assessment
Identification and prioritization of the functions and processes of the organization, in order to determine which will have the greatest impact in the event of unavailability. Assessing the resources needed to support the business impact analysis process. Analysis of the information obtained to identify any gaps between the defined requirements and the organization's ability to meet such requirements
-
Resilience Strategy
Selection of continuity strategies for providing ICT (Information and Communication Technology) systems and services that support critical processes in alternative locations, observing the best cost-effectiveness to reduce deficiencies identified during the risk assessment and analysis process of impact on business.
-
Incident Response
Implementation of a management/response process for incidents and emergencies (including cyber events), containing the critical assets of the organisation that will be monitored alongside the reporting models and the response strategies. This is supported by our proprietary suite for in-depth Digital Forensics.
-
Crisis Management
Development and Implementation of a Crisis Communication Plan. Assurance that the crisis communication plan will provide effective integration with internal and external parties.
-
Disaster Recovery
Documentation , Implementation and Testing of disaster recovery plans (PRD's) to be used during an incident that affects critical ICT systems and services, allowing the organisation to remain operational.
-
Readiness
Support for ongoing management of organisational cyber resilience and continuous assessment of the business continuity management program and identification of opportunities for improvement in controls, helping the organisation to increase its level of maturity.
Coming Soon
UK Wide Cyber Surgeries - get a free one hour consultation to better understand you Cyber Risks and get access to specific services and solutions.
If you are interested contact us below
Accreditation and Compliance
Meeting Globally Recognized Standards

Contact
Contact Us
Location:
St Catherines House, Woodfield Park, Tickhill Road,Doncaster, DN4 8Q9, United Kingdom
Email:
info@assentian.com



















